AUCTORES
Globalize your Research
Research Article | DOI: https://doi.org/10.31579/2690-1897/214
African Institute of Science Administration and Commercial Studies Lome-Togo, Department of Computer Science / Information Technology
*Corresponding Author: Akhigbe-mudu Thursday Ehis, African Institute of Science Administration and Commercial Studies Lome-Togo, Department of Computer Science / Information Technology.
Citation: Akhigbe-Mudu Thursday Ehis, (2024), Enhancing Blockchain (Account Abstraction) Interoperability Based on Transaction Latency Without Truncating Security, J, Surgical Case Reports and Images, 7(10); DOI:10.31579/2690-1897/214
Copyright: © 2024, Akhigbe-Mudu Thursday Ehis. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received: 28 October 2024 | Accepted: 15 November 2024 | Published: 25 November 2024
Keywords: blockchain; cryptographic primitive; interoperability; network congestion; transaction confirmation
Blockchain" refers to a technology that creates a digital record of transactions stored in chronological order as blocks. The main goals of cryptography in the blockchain are to protect users from outside authorities, guarantee participant’s security, and guard against duplicate spending. When the volume of transactions exceeds a network’s capacity, it causes delays in transfer processing, which is known as network overflow. The method for calculating the transaction delay of each latency phase is presented in this paper. The transaction proposals, α bits, experience a transferring delay of α/ℬ + which all clients transmit to the appropriate endorsers. Using the chain-code, the endorsers carry out the transaction proposal. An MEME1 queue with exponential service times with mean 1 /μ and exponential inter arrival times 1/(λα) is used to mimic the execution of the transaction proposal at endorsers. The transaction is completed in the order that it arrives, and equation (4) yields the traffic intensity at the endorser. The suggested method was assessed using a set of signature images, and the results show that it has a high level of accuracy for both signature detection and verification. As evidenced by the results, the recommended based strategy performs better than the traditional approach, with average accuracy in tasks related to signature detection and verification reaching 99.5% and 98.6%, respectively. It further discusses general biometric recognition system concepts, different categorization faults, and how to compare two systems' quality objectively.
A blockchain is a shared, immutable database that facilitates the process of keeping records and tracking these records in a shared environment. Blockchain, thus, is simply a technology that builds a trustworthy service in a not necessarily trustworthy environment (Clavin et al., 2020). Blockchain is a form of distributed ledger technology (DLT) that allows for secure, transparent and immutable storage of information on a network of interconnected computers called nodes. It is a technology that enables the creation of a digital record of transactions or other types of data, which are recorded in blocks that are chained together in chronological order, hence the name “blockchain”. Blockchain is thought to be a developing technology that will enhance security, trust, and transparency for a variety of applications, including information systems. In essence, a blockchain is a distributed ledger that can guarantee data integrity without the need for an intermediary (Hamed Taherdoost 2024). Permissionless and permissioned blockchains are the two basic types of blockchains (Li et al., 2023)). With permissionless (or public) blockchains, like Ethereum and Bitcoin, anyone can take part in the consensus process without revealing their identity. Blockchains with permissions impose stringent membership requirements, allowing only verified nodes to validate transactions and generate new blocks. Moreover, private and consortium blockchains are additional categories into which these permissioned blockchains can be separated (Nkoro et al., 2023). Consortial blockchains are in the middle between the public and private blockchain space, whereas private blockchains are managed by a single entity. Furthermore, the widely used Proof-of-Work (PoW) consensus process in public blockchains is computationally demanding and non-deterministic. On the other hand, the majority of permissioned blockchains use deterministic consensus techniques, which make it simple and quick for verified users to come to an agreement. Because enterprise applications need to execute many transactions in a deterministic way, permissioned blockchains are a great fit for them.
1.1 Transaction Confirmation
Even while interest in cryptocurrencies is growing, one of the things preventing systems like Bitcoin from being widely used is the time it takes for transactions to be confirmed. Although the confirmation times for Bitcoin transactions are typically shorter—minutes—than those of traditional credit card systems, which take seconds.
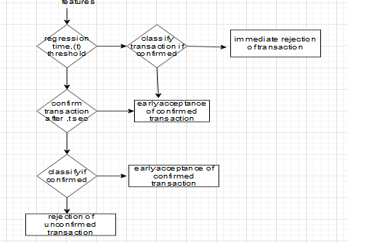
Figure 1: Framework for Transaction Confirmation
Figure 1 shows the suggested framework for transaction classification. The mean confirmation time for a new transaction is obtained by regression analysis based on its attributes. It is worthwhile to wait until the anticipated confirmation time falls below a certain threshold in order to determine whether the transaction will validate itself. The threshold, t, needs to take into consideration both the sensitivity of the delay with regard to various parameters (which can be evaluated, for example, using the proposed queueing theory model) and system requirements (e.g., users' patience). The transaction then generates an early confirmation if it is confirmed by the anticipated time. If not, a classifier is used to determine whether the transaction, which has already taken t seconds to complete in the system—will be confirmed. A classifier of this kind needs to be trained on transactions that have already encountered a system delay that is comparable to or equal to the pre-specified delay. The classifier's output could result in an early acceptance or rejection. It should be noted that the classifier used to determine whether the transaction should be denied right away must take into consideration all of the data that has been made available up to this point if the expected time to confirm the transaction was initially higher than t. A transaction's expenses should also be balanced before it is accepted or rejected since a false positive (identifying a transaction as acceptable, in case it is never confirmed) may
incur different costs than a false negative (classifying a transaction as not acceptable, in case it is eventually confirmed).
1.2 BlockChain Network Congestion
When there are more transactions than the network can handle, it is referred to as blockchain network overload and causes delays in transfer processing. The network gets overloaded when there are more outstanding transactions than the blockchain can handle, as seen in figure 2. The time needed to produce a new block and the block size limitation are the causes of this. Users notice lengthier processing times and delayed transactions. As a result, network overload resulted from the minting of BRC-20 tokens in the Bitcoin blockchain, which caused a dramatic spike in transaction volume. Overload can be caused by a rise in the number of users, high transaction volumes, and special occasions like initial coin offers (ICOs). Prioritizing transactions may result in additional fees for the customer, which would increase costs and decrease efficiency while detracting from the overall user experience. Yet, blockchain networks are always developing new protocols and layer 2 scaling techniques to increase scalability, guarantee seamless transactions, and lessen congestion problems. These efforts are crucial to the broader acceptance of cryptocurrencies because they improve the dependability and effectiveness of blockchains even at times of peak demand.
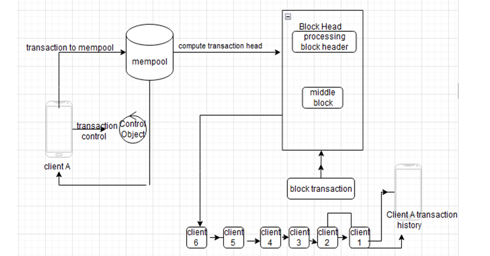
Figure 2: Blockchain Network Congestion
1.3 Statement of the Problem
Because blockchain is a complicated technology, its implementation and upkeep call for a high degree of technical know-how. Difficulties with technology could prevent blockchain technology from becoming widely used and deter developers and users from interacting with it. Although block chain protocols are frequently cited as one of the main advantages of cryptocurrency technology, there are several drawbacks to block chain networks. Blockchain networks have experienced hacker attacks, security lapses, and network overload; these issues can lead to financial losses as well as harm to the network's integrity (Ahakonyee et al., 2023). Even while interest in cryptocurrencies is growing, one of the things preventing systems like Bitcoin from becoming widely used is the time it takes for transactions to be confirmed. Peak traffic on a blockchain network results in backlogs of transactions, delays, and higher transaction fees because miners have a choice in what they process and demand exceeds supply. There could be a wait even if you pay a high transaction charge. The following guidelines guide the discussion of the variables influencing transaction latencies in this paper:
1.3.1 Congestion in the Network: The blockchain network may become overloaded by large transaction volumes, which would cause processing delays. The quantity of outstanding transactions may surge during times of high activity, such as during a well-attended token sale or notable market fluctuations, creating a backlog.
1.3.2 Block Size: Block Size: The number of transactions that can be included in a blockchain block is restricted. Some transactions might need to wait until the next block is confirmed if there are a lot of outstanding ones.
1.3.3 Confirmation Time: The time it takes for a block to be confirmed varies across blockchains. For instance, the average block time for Ethereum is about 15 seconds, whereas it is over 10 minutes for Bitcoin. It is only natural for transactions on blockchains with greater confirmation periods to take longer to confirm.
This paper presents a framework that includes a queueing theory model to (i) identify which transactions will be confirmed and (ii) characterize the confirmation time of confirmed transactions. Transaction delays can be caused by the time it takes for information to travel from one node to another in a blockchain network. Factors like the mean time between transactions and the activity time of blocks are taken into account in the suggested queueing theory model.
1.4 Interoperability
Another major issue facing the sector is interoperability, or the capacity of various blockchain networks to converse and cooperate with one another (Ebuka et al., 2024). Currently, there are a wide variety of blockchain systems, each with own protocols and standards, and they frequently don't cooperate properly. Because people and businesses may need to use several tokens or cryptocurrencies to communicate with various networks, this lack of interoperability might result in inefficiencies. Additionally, this fragmentation may make it more difficult to work together, discourage innovation, and impede the smooth transfer of wealth and data between various blockchain ecosystems. To fully realize the potential of blockchain technology, it will be imperative to foster interoperability among various networks as the sector grows and diversifies. Through dismantling silos and encouraging cooperation amongst different blockchain platforms, the industry may strive to build a unified, effective, and inclusive digital environment that helps businesses, developers, and users.
1.5 Privacy and data protection
Interoperability, or the ability of different blockchain networks to communicate and collaborate with one another, is another significant problem facing the industry. There are many different blockchain systems available today, each with its own standards and protocols, and they often don't work together correctly (Chinaechetan et al., 2024). The inability of individuals or companies to communicate with different networks using several tokens or cryptocurrencies could lead to inefficiencies. Furthermore, this fragmentation can hinder collaboration, stifle creativity, and obstruct the easy flow of money and data between different blockchain ecosystems. As the industry expands and becomes more diverse, it will be crucial to promote interoperability across different networks in order to fully exploit the promise of blockchain technology. These blockchains store records that protect user privacy, with user data security at the core of their design. Since the public may not always access or view their data and records, permissioned blockchains are typically privacy-preserving. A private network does not, however, always protect privacy. The concept of privacy preserving networks considers whether the network's records are easily accessible and readable by everyone or whether they are obfuscated. In contrast to publicly permissionless networks, which are defined by their permissioned or proprietary nature, private networks are thought to be better concealed. Therefore, networks that are private, permissioned, or proprietary deal with network ownership, but networks that preserve privacy deal with the data protection of records on that specific network.
2. 0 Literature Review
Many recent works mentioned the performance issue of blockchain platforms as a promising research and explored the performance from experimental and theoretical analysis (Bolfing 2020). In this section, the latency transaction researches related to blockchain are discussed. In Petros et al., (2024), the authors provided a scalability, throughput, average latency, and execution time performance analysis. The experiment results allowed the authors to determine how blockcahin performed in different experimental scenarios. In a thorough performance experiment, the authors of Sine et al., (2023) varied the values assigned to the system's customizable parameters, such as transaction arrival rate, block size, endorsement policy, channel numbers, and resource allocation. Additionally, recommendations for setting choices were made in order to get the best performance possible for their works. Moreover, Tien Tuan et al. proposed BLOCKBENCH in Clavin et al. (2020), the first evaluation framework of private blockchain systems to analyze the performance of permissioned block-chain systems. In BLOCKBENCH, the blockchain architecture was divided into three modular layers, i.e., the consensus layer, the data model layer, and the execution layer. Bolfing (2020) discussed the performance and scalability characteristics of blockchain using an experimental approach. Under different sets of workloads, authors studied how configuration parameters (transaction-related and chain code-related) influence the overall throughput and latency metrics in blockchain. The outcomes of their experiments demonstrated that the Fabric blockchain continuously outperformed the other two systems in terms of performance. The outcomes also showed certain bottlenecks and the limitations of the Fabric blockchain in managing workloads related to data processing. By altering the network layer delays, the authors of Nkoro et al., (2024) assessed the Fabric blockchain's performance. They set up two cloud data centers with a Fabric blockchain network and added transmission delays of up to G.Ks. The trials revealed that when delays exceeded G.Ks, the Fabric blockchain system abruptly stopped, demonstrating how even tiny network delays can have a significant effect on the system's performance. In addition, authors in Wong et al., (2019) created patterns of malicious conduct taking into account the malicious behaviors of the Fabric blockchain system. According to the experimental results, Fabric V1.B, which uses the execute-order-validate paradigm, can withstand attacks by transactions that have an indefinite loop, but Fabric V0.6 was unable to withstand denial-of-service attacks. The aforementioned studies solely used empirical metrics to analyze performance in the Fabric blockchain; no theoretical analysis was done to offer a quantitative framework. Furthermore, because of the numerous configuration possibilities and intricate underlying network settings, these empirical data could not be compared. Numerous earlier papers have addressed theoretical performance analysis in response to these difficulties. To determine the mean finishing time of the PBFT consensus process (Kuizhi et at., 2023) in Fabric, Sa’ad Zyoud (2024) developed a theoretic model based on Stochastic Reward Nets (SRN). Performance metrics under different configuration factors were estimated using this model. This theoretical modeling provided various possible Fabric blockchain performance bottlenecks and computed the average latency during PBFT consensus. Nevertheless, neither the comprehensive explanation of the model nor the overall latency analysis were included in this analysis model. Thus, the extending work was presented in Song et al., (2023). Authors suggested using the Generalized Stochastic Petri Nets (GSPN) method in li et al., (2020) and the analytic-numeric solution (SPNP) to theoretically analyze the subsystem corresponding to each transaction phase in the Fabric blockchain. It is true that this SRN-based theoretical model can estimate the Fabric V1.0 blockchain's overall latency performance but it cannot compute the latency at a specific transaction arrival rate and does not account for any queuing delays at various nodes.
3.1 Queuing Model
A simple queueing model to capture the relationship between different quantities that together impact delays in a blockchain system is hereby proposed. Figure 3 illustrates the key quantities of interest in the queueing model.
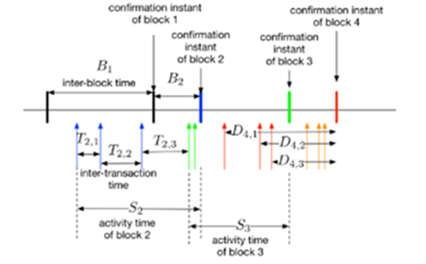
Figure 3: Queuing Model
3.1.1 Workload
Consider a flow of transactions that arrive at rate λ to the system. Each transaction is part of a block. Blocks are mined at rate λ B blocks/s, and
each block comprises an average of τ transactions. Assume a system under equilibrium, neglecting unconfirmed transactions in our queueing model (Love Allen et al., 2024). Therefore, there is a flow of λ = λB τ transactions served per time unit.
3.1.2 Active blocks and block confirmation times
Then, we introduce the notion of the active time of a block. The active time of a block initiates when the first transaction to eventually be confirmed in a block is issued, and finishes when that block is confirmed. It is denoted by ‘S’ the active time of a block, and by ‘M’ the number of active blocks in the system. The active time of block Si denotes me. It follows from Little’s law that,
E(M ) = λB E(S). (1)
Let B denote the time between block confirmations. It follows that E(B) = 1/λB . Let T be the intertransaction time denoted by E(B) = 1/λB, the time j-th is the transaction arrival, following the (j−1)th arrival of a transaction served in the i-th block.
3.1.3 Transaction delays and delay model
‘D’ denotes the delay incurred by a typical user transaction. In particular, 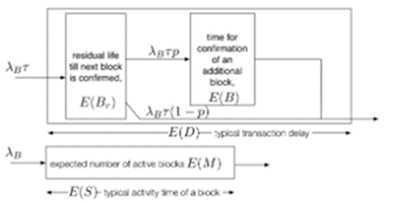 is the delay incurred by the j-th transaction that was confirmed in Blocki. The delay is assumed to be assessed by a user that samples the network at an arbitrary point in time, chosen uniformly at random (allowing us to use renewal theory arguments) (Gupta et al., 2019). We assume that system inspection occurs uniformly at random. Then, our model for the delay experienced by a user is given by
is the delay incurred by the j-th transaction that was confirmed in Blocki. The delay is assumed to be assessed by a user that samples the network at an arbitrary point in time, chosen uniformly at random (allowing us to use renewal theory arguments) (Gupta et al., 2019). We assume that system inspection occurs uniformly at random. Then, our model for the delay experienced by a user is given by
E (D) = αE (B) + E (Br), 2 where
 3
3
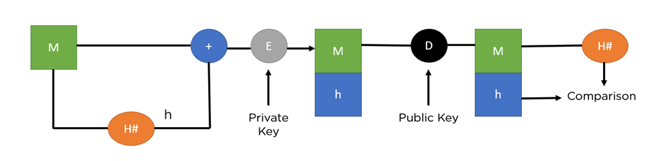
Represents the inter-block time's residual time. The expected number of blocks a user must wait for a transaction to be confirmed is indicated by parameter α. Remember that, as stated in Section 2, we consider a transaction to be confirmed whenever its block is appended to the blockchain. Keep in mind that αE(B) represents the amount of time a user must wait in addition to the block's residual life when they initially enter the system. The basic M/G/1 model inspires equation (2). The M/G/1 model represents the likelihood that the system is busy now of a new arrival by having the coefficient of residual service time equal to the system utilization. In contrast, our model maintains stability as an open research issue since a block is always being mined at the system (Magnus et al., (2020). It is observed from the measurements that α is generally less than 1. As a result, it offers a different reading of the model, as seen in Figure 4. This statistic indicates that each user must wait for a block's residual life. Users also have to wait for the confirmation of an extra block with probability p. Next, 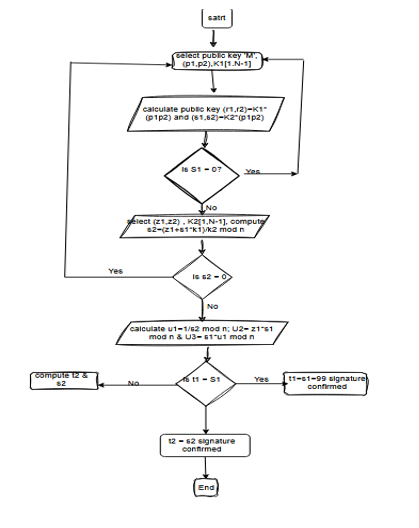
where 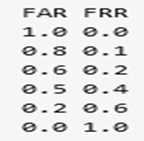
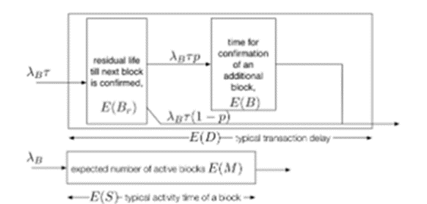
Figure 4: Illustrating Transaction Latency
3.2 Transaction Flow
Every successfully committed transaction in the Fabric blockchain goes through three stages. Transaction proposals are first approved and carried out. Second, a consensus process is used by the ordering service to order these transactions. Ultimately, all peers do transaction validation in order to avoid conflicts brought on by concurrency. We then go into great depth about these three stages.
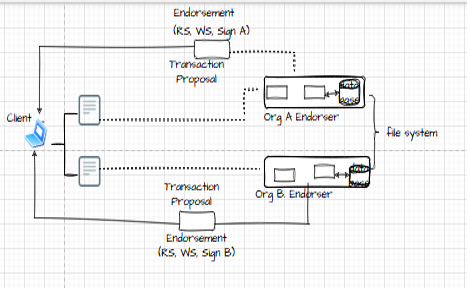
3.3 Phase of Execution. To be executed, clients submit transaction proposals to a group of endorsers. A transaction proposal signed with the client's identity is forwarded, as seen in Fig. 5, to one or more peers in accordance with the endorsement policy. To generate endorsements in the form of read sets (RS) and write sets (WS), each endorser carries out the transaction using a pre-installed chaincode (Nwakanma et al., 2023)
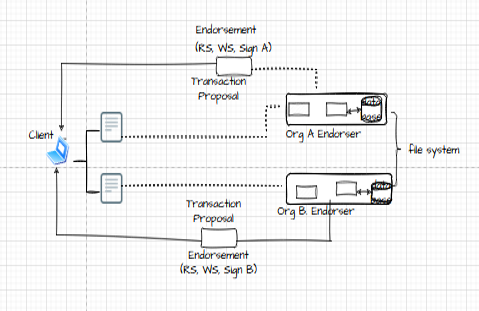
Figure 5: The execution phase (Zou et a., 2022).
The transaction proposal is sent by the client to endorsers, who then carry it out using pre-installed chaincode. Subsequently, the client receives an endorsement that includes WS, RS, and one signature (Sign A or Sign B). Endorsers then return the cryptographically signed endorsements to the client as part of a proposal response. The client receives a sufficient number of testimonials from the referrers and confirms the consistency of the testimonials. Clients create transactions and forward them to the ordering service (Nitsesha et al., 2022). The channel ID, endorsements, transaction payload, and transaction information make up a transaction. The ordering service first establishes consensus and a total order for all transactions per channel using a pluggable consensus approach, all without looking at the contents of individual transactions. After then, the ordering service uses the gossip protocol to send blocks of ordered transactions to peers. Blocks are sent by the ordering service to all peers, endorsers and committers, who then decode them. Next, the validation system chaincode (VSCC) is applied to each transaction within a block. Finally, validation of multi-version concurrency control (MVCC) will be carried out.
3.4 Latency performance modeling
In this section, we present the theoretical latency analysis of Fabric blockchain. First introduce the system model used in the analysis, then propose a detailed latency calculation of the single-channel (Roylan et al., 2023). Fabric in full accordance with the execute-order-validate transaction. Finally, the latency analysis of the multi-channel Fabric will be discussed.
3.5. System model
Consider a Fabric blockchain system with the Solo consensus mechanism. We assume that the transactions are generated by M clients and broadcast across the Fabric network, which is made up of K organizations with N peers for each organization (Georgios et al., 2023). The arrival of new transactions follows the Poisson Point Process with the arrival rate λ. Each transaction has a packet size of α bits, and one signature has a size of γ bits. The endorsement policy requires that each transaction be executed
on Ne endorsers, and the endorsement policy specifies that each transaction must be executed on Ne endorsers. Additionally, we define that the blockchain network has ℬ bps bandwidth for the bottleneck link and that the average propagation delay is
These characteristics are used by the signature detection module to determine whether a signature is present in the image. Lastly, the signature verification module compares the signature to the reference signature to confirm the signature's legitimacy. A collection of signature images was used to analyze the suggested method, and the findings demonstrate its high degree of accuracy in both signature detection and verification. The system has a number of possible uses in the authentication and verification of documents. In this paper, the use of convolutional neural networks (CNNs), a type of deep learning technique, for signature verification and detection is explored. Using a sizable dataset of signature images, it trained a CNN model and evaluated its results against the conventional method. The outcomes demonstrate that the proposed method outperforms the conventional method, with average accuracy in signature detection and verification tasks reaching 99.5% and 98.6%, respectively. Our suggested method for digital image signature identification and verification works well and has a wide range of real-world uses.
4.1 Evaluation
Security Testing (Confidentiality)
False Acceptance Rate (FAR), a measure of how frequently a system allows access to an unauthorized user, is used in biometric security. FAR is referred to as Type II mistake in statistics.
4.1.1 Rate of False Rejections
The percentage of times a biometric system denies access to a person who is permitted is known as the False Rejection Rate, or FRR. FRR is referred to as Type I error in statistics.
4.1.2 Rate of Crossover Errors
Examining a biometric security system's Crossover Error Rate (CER), sometimes referred to as the Equal Error Rate (EER), is one approach to condense its operational features. The FAR and FRR of the system can be changed by adjusting certain system parameters. To get the FAR and FRR to equalize, adjust these. The CER or EER is their shared value when the two are equal. The CER provides a means of system comparison. The better, the lower the CER. When the CER value is lower, the system can be tuned to have lower Type I and Type II error rates than it would have with a different setup.

FAR and FRR metrics includes:
FA (Falsely Accepted) – number of forged examples Accepted as genuine
TR (Truly rejected) – number of forged examples rejected as false
FR (Falsely rejected) – number of genuine examples accepted as forged
TA (Truly Accepted) – the number of genuine examples accepted as genuine
4.1.3 Calculate FFR, FAR and EER
Determine the rates of false acceptance and rejection (Yu Sun et al., 2023). It will load the test data, which consists of more than 200 images, crop the faces, store them in a numpy array, and then encode the images in the same way that we did with the train test data. The train test data contains images that are 50% real and 50% imposter.
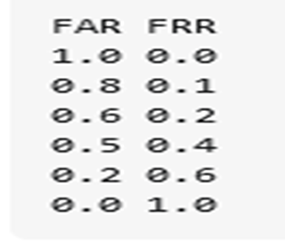
4.1.4 Crossover error rate (CER)
The intersection of the false reject rate (FRR) and false accept rate (FAR) is described by the crossover error rate. The equal error rate (EER) is another name for CER. The crossover error rate provides an overview of a biometric system's overall accuracy (Akanni 2021). FRRs will grow and FARs will fall as a biometric system's sensitivity rises. On the other hand, FRRs will decrease and FARs will increase as the sensitivity is decreased (Alsirhani et al., 2023) A graph that compares FARs and FRRs is presented in Figure 8. The graph in Figure 8, which is based on Auditing Guideline is Biometric Controls (Vivek et al., 2023), has two lines that overlap at the CER.
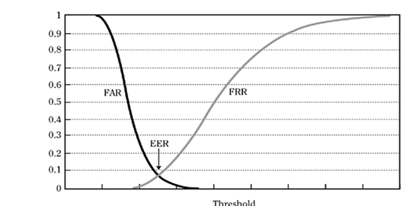
Figure 8: The Biometric Security Characteristics
The FAR curve shows the scenario in which an impostor can be recognized as authentic and passes at the threshold of 0. As the threshold is raised, the impostor's chances of passing decrease (Lindani & Tanja 2023). The FRR curve shows what happens when the original is refused; as the threshold is raised, the original's chance of being rejected rises to the point where it passes 100% of the time, and this decreases as the threshold is raised. Since the optimal value is closest to zero, the point of EER represents the best threshold to select. It is the point where FAR and FRR meet. Developing the facial recognition technology and figuring out the FAR, FRR, and EER.
Even though interest in cryptocurrencies is growing, one of the things preventing systems latency from being widely adopted is the time it takes for transactions to be confirm’oed. Peak traffic on a blockchain network results in backlogs of transactions, delays, and increased transaction fees since demand exceeds supply. The calculation of each phase's transaction latency is explained in this document. The execution phase's latency: The execution phase consists of three steps, as Fig. 5 illustrates. (i) Every client forwards the proposed transactions to the appropriate endorsers. Transaction proposals with α bits are sent by the clients; their transferring latency is α/ℬ +
Clearly Auctoresonline and particularly Psychology and Mental Health Care Journal is dedicated to improving health care services for individuals and populations. The editorial boards' ability to efficiently recognize and share the global importance of health literacy with a variety of stakeholders. Auctoresonline publishing platform can be used to facilitate of optimal client-based services and should be added to health care professionals' repertoire of evidence-based health care resources.

Journal of Clinical Cardiology and Cardiovascular Intervention The submission and review process was adequate. However I think that the publication total value should have been enlightened in early fases. Thank you for all.

Journal of Women Health Care and Issues By the present mail, I want to say thank to you and tour colleagues for facilitating my published article. Specially thank you for the peer review process, support from the editorial office. I appreciate positively the quality of your journal.
Journal of Clinical Research and Reports I would be very delighted to submit my testimonial regarding the reviewer board and the editorial office. The reviewer board were accurate and helpful regarding any modifications for my manuscript. And the editorial office were very helpful and supportive in contacting and monitoring with any update and offering help. It was my pleasure to contribute with your promising Journal and I am looking forward for more collaboration.

We would like to thank the Journal of Thoracic Disease and Cardiothoracic Surgery because of the services they provided us for our articles. The peer-review process was done in a very excellent time manner, and the opinions of the reviewers helped us to improve our manuscript further. The editorial office had an outstanding correspondence with us and guided us in many ways. During a hard time of the pandemic that is affecting every one of us tremendously, the editorial office helped us make everything easier for publishing scientific work. Hope for a more scientific relationship with your Journal.

The peer-review process which consisted high quality queries on the paper. I did answer six reviewers’ questions and comments before the paper was accepted. The support from the editorial office is excellent.

Journal of Neuroscience and Neurological Surgery. I had the experience of publishing a research article recently. The whole process was simple from submission to publication. The reviewers made specific and valuable recommendations and corrections that improved the quality of my publication. I strongly recommend this Journal.

Dr. Katarzyna Byczkowska My testimonial covering: "The peer review process is quick and effective. The support from the editorial office is very professional and friendly. Quality of the Clinical Cardiology and Cardiovascular Interventions is scientific and publishes ground-breaking research on cardiology that is useful for other professionals in the field.

Thank you most sincerely, with regard to the support you have given in relation to the reviewing process and the processing of my article entitled "Large Cell Neuroendocrine Carcinoma of The Prostate Gland: A Review and Update" for publication in your esteemed Journal, Journal of Cancer Research and Cellular Therapeutics". The editorial team has been very supportive.

Testimony of Journal of Clinical Otorhinolaryngology: work with your Reviews has been a educational and constructive experience. The editorial office were very helpful and supportive. It was a pleasure to contribute to your Journal.

Dr. Bernard Terkimbi Utoo, I am happy to publish my scientific work in Journal of Women Health Care and Issues (JWHCI). The manuscript submission was seamless and peer review process was top notch. I was amazed that 4 reviewers worked on the manuscript which made it a highly technical, standard and excellent quality paper. I appreciate the format and consideration for the APC as well as the speed of publication. It is my pleasure to continue with this scientific relationship with the esteem JWHCI.

This is an acknowledgment for peer reviewers, editorial board of Journal of Clinical Research and Reports. They show a lot of consideration for us as publishers for our research article “Evaluation of the different factors associated with side effects of COVID-19 vaccination on medical students, Mutah university, Al-Karak, Jordan”, in a very professional and easy way. This journal is one of outstanding medical journal.
Dear Hao Jiang, to Journal of Nutrition and Food Processing We greatly appreciate the efficient, professional and rapid processing of our paper by your team. If there is anything else we should do, please do not hesitate to let us know. On behalf of my co-authors, we would like to express our great appreciation to editor and reviewers.

As an author who has recently published in the journal "Brain and Neurological Disorders". I am delighted to provide a testimonial on the peer review process, editorial office support, and the overall quality of the journal. The peer review process at Brain and Neurological Disorders is rigorous and meticulous, ensuring that only high-quality, evidence-based research is published. The reviewers are experts in their fields, and their comments and suggestions were constructive and helped improve the quality of my manuscript. The review process was timely and efficient, with clear communication from the editorial office at each stage. The support from the editorial office was exceptional throughout the entire process. The editorial staff was responsive, professional, and always willing to help. They provided valuable guidance on formatting, structure, and ethical considerations, making the submission process seamless. Moreover, they kept me informed about the status of my manuscript and provided timely updates, which made the process less stressful. The journal Brain and Neurological Disorders is of the highest quality, with a strong focus on publishing cutting-edge research in the field of neurology. The articles published in this journal are well-researched, rigorously peer-reviewed, and written by experts in the field. The journal maintains high standards, ensuring that readers are provided with the most up-to-date and reliable information on brain and neurological disorders. In conclusion, I had a wonderful experience publishing in Brain and Neurological Disorders. The peer review process was thorough, the editorial office provided exceptional support, and the journal's quality is second to none. I would highly recommend this journal to any researcher working in the field of neurology and brain disorders.

Dear Agrippa Hilda, Journal of Neuroscience and Neurological Surgery, Editorial Coordinator, I trust this message finds you well. I want to extend my appreciation for considering my article for publication in your esteemed journal. I am pleased to provide a testimonial regarding the peer review process and the support received from your editorial office. The peer review process for my paper was carried out in a highly professional and thorough manner. The feedback and comments provided by the authors were constructive and very useful in improving the quality of the manuscript. This rigorous assessment process undoubtedly contributes to the high standards maintained by your journal.

International Journal of Clinical Case Reports and Reviews. I strongly recommend to consider submitting your work to this high-quality journal. The support and availability of the Editorial staff is outstanding and the review process was both efficient and rigorous.

Thank you very much for publishing my Research Article titled “Comparing Treatment Outcome Of Allergic Rhinitis Patients After Using Fluticasone Nasal Spray And Nasal Douching" in the Journal of Clinical Otorhinolaryngology. As Medical Professionals we are immensely benefited from study of various informative Articles and Papers published in this high quality Journal. I look forward to enriching my knowledge by regular study of the Journal and contribute my future work in the field of ENT through the Journal for use by the medical fraternity. The support from the Editorial office was excellent and very prompt. I also welcome the comments received from the readers of my Research Article.

Dear Erica Kelsey, Editorial Coordinator of Cancer Research and Cellular Therapeutics Our team is very satisfied with the processing of our paper by your journal. That was fast, efficient, rigorous, but without unnecessary complications. We appreciated the very short time between the submission of the paper and its publication on line on your site.

I am very glad to say that the peer review process is very successful and fast and support from the Editorial Office. Therefore, I would like to continue our scientific relationship for a long time. And I especially thank you for your kindly attention towards my article. Have a good day!

"We recently published an article entitled “Influence of beta-Cyclodextrins upon the Degradation of Carbofuran Derivatives under Alkaline Conditions" in the Journal of “Pesticides and Biofertilizers” to show that the cyclodextrins protect the carbamates increasing their half-life time in the presence of basic conditions This will be very helpful to understand carbofuran behaviour in the analytical, agro-environmental and food areas. We greatly appreciated the interaction with the editor and the editorial team; we were particularly well accompanied during the course of the revision process, since all various steps towards publication were short and without delay".

I would like to express my gratitude towards you process of article review and submission. I found this to be very fair and expedient. Your follow up has been excellent. I have many publications in national and international journal and your process has been one of the best so far. Keep up the great work.

We are grateful for this opportunity to provide a glowing recommendation to the Journal of Psychiatry and Psychotherapy. We found that the editorial team were very supportive, helpful, kept us abreast of timelines and over all very professional in nature. The peer review process was rigorous, efficient and constructive that really enhanced our article submission. The experience with this journal remains one of our best ever and we look forward to providing future submissions in the near future.

I am very pleased to serve as EBM of the journal, I hope many years of my experience in stem cells can help the journal from one way or another. As we know, stem cells hold great potential for regenerative medicine, which are mostly used to promote the repair response of diseased, dysfunctional or injured tissue using stem cells or their derivatives. I think Stem Cell Research and Therapeutics International is a great platform to publish and share the understanding towards the biology and translational or clinical application of stem cells.

I would like to give my testimony in the support I have got by the peer review process and to support the editorial office where they were of asset to support young author like me to be encouraged to publish their work in your respected journal and globalize and share knowledge across the globe. I really give my great gratitude to your journal and the peer review including the editorial office.

I am delighted to publish our manuscript entitled "A Perspective on Cocaine Induced Stroke - Its Mechanisms and Management" in the Journal of Neuroscience and Neurological Surgery. The peer review process, support from the editorial office, and quality of the journal are excellent. The manuscripts published are of high quality and of excellent scientific value. I recommend this journal very much to colleagues.

Dr.Tania Muñoz, My experience as researcher and author of a review article in The Journal Clinical Cardiology and Interventions has been very enriching and stimulating. The editorial team is excellent, performs its work with absolute responsibility and delivery. They are proactive, dynamic and receptive to all proposals. Supporting at all times the vast universe of authors who choose them as an option for publication. The team of review specialists, members of the editorial board, are brilliant professionals, with remarkable performance in medical research and scientific methodology. Together they form a frontline team that consolidates the JCCI as a magnificent option for the publication and review of high-level medical articles and broad collective interest. I am honored to be able to share my review article and open to receive all your comments.

“The peer review process of JPMHC is quick and effective. Authors are benefited by good and professional reviewers with huge experience in the field of psychology and mental health. The support from the editorial office is very professional. People to contact to are friendly and happy to help and assist any query authors might have. Quality of the Journal is scientific and publishes ground-breaking research on mental health that is useful for other professionals in the field”.

Dear editorial department: On behalf of our team, I hereby certify the reliability and superiority of the International Journal of Clinical Case Reports and Reviews in the peer review process, editorial support, and journal quality. Firstly, the peer review process of the International Journal of Clinical Case Reports and Reviews is rigorous, fair, transparent, fast, and of high quality. The editorial department invites experts from relevant fields as anonymous reviewers to review all submitted manuscripts. These experts have rich academic backgrounds and experience, and can accurately evaluate the academic quality, originality, and suitability of manuscripts. The editorial department is committed to ensuring the rigor of the peer review process, while also making every effort to ensure a fast review cycle to meet the needs of authors and the academic community. Secondly, the editorial team of the International Journal of Clinical Case Reports and Reviews is composed of a group of senior scholars and professionals with rich experience and professional knowledge in related fields. The editorial department is committed to assisting authors in improving their manuscripts, ensuring their academic accuracy, clarity, and completeness. Editors actively collaborate with authors, providing useful suggestions and feedback to promote the improvement and development of the manuscript. We believe that the support of the editorial department is one of the key factors in ensuring the quality of the journal. Finally, the International Journal of Clinical Case Reports and Reviews is renowned for its high- quality articles and strict academic standards. The editorial department is committed to publishing innovative and academically valuable research results to promote the development and progress of related fields. The International Journal of Clinical Case Reports and Reviews is reasonably priced and ensures excellent service and quality ratio, allowing authors to obtain high-level academic publishing opportunities in an affordable manner. I hereby solemnly declare that the International Journal of Clinical Case Reports and Reviews has a high level of credibility and superiority in terms of peer review process, editorial support, reasonable fees, and journal quality. Sincerely, Rui Tao.

Clinical Cardiology and Cardiovascular Interventions I testity the covering of the peer review process, support from the editorial office, and quality of the journal.

Clinical Cardiology and Cardiovascular Interventions, we deeply appreciate the interest shown in our work and its publication. It has been a true pleasure to collaborate with you. The peer review process, as well as the support provided by the editorial office, have been exceptional, and the quality of the journal is very high, which was a determining factor in our decision to publish with you.
The peer reviewers process is quick and effective, the supports from editorial office is excellent, the quality of journal is high. I would like to collabroate with Internatioanl journal of Clinical Case Reports and Reviews journal clinically in the future time.

Clinical Cardiology and Cardiovascular Interventions, I would like to express my sincerest gratitude for the trust placed in our team for the publication in your journal. It has been a true pleasure to collaborate with you on this project. I am pleased to inform you that both the peer review process and the attention from the editorial coordination have been excellent. Your team has worked with dedication and professionalism to ensure that your publication meets the highest standards of quality. We are confident that this collaboration will result in mutual success, and we are eager to see the fruits of this shared effort.

Dear Dr. Jessica Magne, Editorial Coordinator 0f Clinical Cardiology and Cardiovascular Interventions, I hope this message finds you well. I want to express my utmost gratitude for your excellent work and for the dedication and speed in the publication process of my article titled "Navigating Innovation: Qualitative Insights on Using Technology for Health Education in Acute Coronary Syndrome Patients." I am very satisfied with the peer review process, the support from the editorial office, and the quality of the journal. I hope we can maintain our scientific relationship in the long term.
Dear Monica Gissare, - Editorial Coordinator of Nutrition and Food Processing. ¨My testimony with you is truly professional, with a positive response regarding the follow-up of the article and its review, you took into account my qualities and the importance of the topic¨.

Dear Dr. Jessica Magne, Editorial Coordinator 0f Clinical Cardiology and Cardiovascular Interventions, The review process for the article “The Handling of Anti-aggregants and Anticoagulants in the Oncologic Heart Patient Submitted to Surgery” was extremely rigorous and detailed. From the initial submission to the final acceptance, the editorial team at the “Journal of Clinical Cardiology and Cardiovascular Interventions” demonstrated a high level of professionalism and dedication. The reviewers provided constructive and detailed feedback, which was essential for improving the quality of our work. Communication was always clear and efficient, ensuring that all our questions were promptly addressed. The quality of the “Journal of Clinical Cardiology and Cardiovascular Interventions” is undeniable. It is a peer-reviewed, open-access publication dedicated exclusively to disseminating high-quality research in the field of clinical cardiology and cardiovascular interventions. The journal's impact factor is currently under evaluation, and it is indexed in reputable databases, which further reinforces its credibility and relevance in the scientific field. I highly recommend this journal to researchers looking for a reputable platform to publish their studies.

Dear Editorial Coordinator of the Journal of Nutrition and Food Processing! "I would like to thank the Journal of Nutrition and Food Processing for including and publishing my article. The peer review process was very quick, movement and precise. The Editorial Board has done an extremely conscientious job with much help, valuable comments and advices. I find the journal very valuable from a professional point of view, thank you very much for allowing me to be part of it and I would like to participate in the future!”

Dealing with The Journal of Neurology and Neurological Surgery was very smooth and comprehensive. The office staff took time to address my needs and the response from editors and the office was prompt and fair. I certainly hope to publish with this journal again.Their professionalism is apparent and more than satisfactory. Susan Weiner

My Testimonial Covering as fellowing: Lin-Show Chin. The peer reviewers process is quick and effective, the supports from editorial office is excellent, the quality of journal is high. I would like to collabroate with Internatioanl journal of Clinical Case Reports and Reviews.

My experience publishing in Psychology and Mental Health Care was exceptional. The peer review process was rigorous and constructive, with reviewers providing valuable insights that helped enhance the quality of our work. The editorial team was highly supportive and responsive, making the submission process smooth and efficient. The journal's commitment to high standards and academic rigor makes it a respected platform for quality research. I am grateful for the opportunity to publish in such a reputable journal.
My experience publishing in International Journal of Clinical Case Reports and Reviews was exceptional. I Come forth to Provide a Testimonial Covering the Peer Review Process and the editorial office for the Professional and Impartial Evaluation of the Manuscript.

I would like to offer my testimony in the support. I have received through the peer review process and support the editorial office where they are to support young authors like me, encourage them to publish their work in your esteemed journals, and globalize and share knowledge globally. I really appreciate your journal, peer review, and editorial office.
Dear Agrippa Hilda- Editorial Coordinator of Journal of Neuroscience and Neurological Surgery, "The peer review process was very quick and of high quality, which can also be seen in the articles in the journal. The collaboration with the editorial office was very good."

I would like to express my sincere gratitude for the support and efficiency provided by the editorial office throughout the publication process of my article, “Delayed Vulvar Metastases from Rectal Carcinoma: A Case Report.” I greatly appreciate the assistance and guidance I received from your team, which made the entire process smooth and efficient. The peer review process was thorough and constructive, contributing to the overall quality of the final article. I am very grateful for the high level of professionalism and commitment shown by the editorial staff, and I look forward to maintaining a long-term collaboration with the International Journal of Clinical Case Reports and Reviews.
To Dear Erin Aust, I would like to express my heartfelt appreciation for the opportunity to have my work published in this esteemed journal. The entire publication process was smooth and well-organized, and I am extremely satisfied with the final result. The Editorial Team demonstrated the utmost professionalism, providing prompt and insightful feedback throughout the review process. Their clear communication and constructive suggestions were invaluable in enhancing my manuscript, and their meticulous attention to detail and dedication to quality are truly commendable. Additionally, the support from the Editorial Office was exceptional. From the initial submission to the final publication, I was guided through every step of the process with great care and professionalism. The team's responsiveness and assistance made the entire experience both easy and stress-free. I am also deeply impressed by the quality and reputation of the journal. It is an honor to have my research featured in such a respected publication, and I am confident that it will make a meaningful contribution to the field.

"I am grateful for the opportunity of contributing to [International Journal of Clinical Case Reports and Reviews] and for the rigorous review process that enhances the quality of research published in your esteemed journal. I sincerely appreciate the time and effort of your team who have dedicatedly helped me in improvising changes and modifying my manuscript. The insightful comments and constructive feedback provided have been invaluable in refining and strengthening my work".

I thank the ‘Journal of Clinical Research and Reports’ for accepting this article for publication. This is a rigorously peer reviewed journal which is on all major global scientific data bases. I note the review process was prompt, thorough and professionally critical. It gave us an insight into a number of important scientific/statistical issues. The review prompted us to review the relevant literature again and look at the limitations of the study. The peer reviewers were open, clear in the instructions and the editorial team was very prompt in their communication. This journal certainly publishes quality research articles. I would recommend the journal for any future publications.

Dear Jessica Magne, with gratitude for the joint work. Fast process of receiving and processing the submitted scientific materials in “Clinical Cardiology and Cardiovascular Interventions”. High level of competence of the editors with clear and correct recommendations and ideas for enriching the article.

We found the peer review process quick and positive in its input. The support from the editorial officer has been very agile, always with the intention of improving the article and taking into account our subsequent corrections.

My article, titled 'No Way Out of the Smartphone Epidemic Without Considering the Insights of Brain Research,' has been republished in the International Journal of Clinical Case Reports and Reviews. The review process was seamless and professional, with the editors being both friendly and supportive. I am deeply grateful for their efforts.
To Dear Erin Aust – Editorial Coordinator of Journal of General Medicine and Clinical Practice! I declare that I am absolutely satisfied with your work carried out with great competence in following the manuscript during the various stages from its receipt, during the revision process to the final acceptance for publication. Thank Prof. Elvira Farina

Dear Jessica, and the super professional team of the ‘Clinical Cardiology and Cardiovascular Interventions’ I am sincerely grateful to the coordinated work of the journal team for the no problem with the submission of my manuscript: “Cardiometabolic Disorders in A Pregnant Woman with Severe Preeclampsia on the Background of Morbid Obesity (Case Report).” The review process by 5 experts was fast, and the comments were professional, which made it more specific and academic, and the process of publication and presentation of the article was excellent. I recommend that my colleagues publish articles in this journal, and I am interested in further scientific cooperation. Sincerely and best wishes, Dr. Oleg Golyanovskiy.

Dear Ashley Rosa, Editorial Coordinator of the journal - Psychology and Mental Health Care. " The process of obtaining publication of my article in the Psychology and Mental Health Journal was positive in all areas. The peer review process resulted in a number of valuable comments, the editorial process was collaborative and timely, and the quality of this journal has been quickly noticed, resulting in alternative journals contacting me to publish with them." Warm regards, Susan Anne Smith, PhD. Australian Breastfeeding Association.

Dear Jessica Magne, Editorial Coordinator, Clinical Cardiology and Cardiovascular Interventions, Auctores Publishing LLC. I appreciate the journal (JCCI) editorial office support, the entire team leads were always ready to help, not only on technical front but also on thorough process. Also, I should thank dear reviewers’ attention to detail and creative approach to teach me and bring new insights by their comments. Surely, more discussions and introduction of other hemodynamic devices would provide better prevention and management of shock states. Your efforts and dedication in presenting educational materials in this journal are commendable. Best wishes from, Farahnaz Fallahian.
Dear Maria Emerson, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews, Auctores Publishing LLC. I am delighted to have published our manuscript, "Acute Colonic Pseudo-Obstruction (ACPO): A rare but serious complication following caesarean section." I want to thank the editorial team, especially Maria Emerson, for their prompt review of the manuscript, quick responses to queries, and overall support. Yours sincerely Dr. Victor Olagundoye.

Dear Ashley Rosa, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews. Many thanks for publishing this manuscript after I lost confidence the editors were most helpful, more than other journals Best wishes from, Susan Anne Smith, PhD. Australian Breastfeeding Association.

Dear Agrippa Hilda, Editorial Coordinator, Journal of Neuroscience and Neurological Surgery. The entire process including article submission, review, revision, and publication was extremely easy. The journal editor was prompt and helpful, and the reviewers contributed to the quality of the paper. Thank you so much! Eric Nussbaum, MD
Dr Hala Al Shaikh This is to acknowledge that the peer review process for the article ’ A Novel Gnrh1 Gene Mutation in Four Omani Male Siblings, Presentation and Management ’ sent to the International Journal of Clinical Case Reports and Reviews was quick and smooth. The editorial office was prompt with easy communication.

Dear Erin Aust, Editorial Coordinator, Journal of General Medicine and Clinical Practice. We are pleased to share our experience with the “Journal of General Medicine and Clinical Practice”, following the successful publication of our article. The peer review process was thorough and constructive, helping to improve the clarity and quality of the manuscript. We are especially thankful to Ms. Erin Aust, the Editorial Coordinator, for her prompt communication and continuous support throughout the process. Her professionalism ensured a smooth and efficient publication experience. The journal upholds high editorial standards, and we highly recommend it to fellow researchers seeking a credible platform for their work. Best wishes By, Dr. Rakhi Mishra.

Dear Jessica Magne, Editorial Coordinator, Clinical Cardiology and Cardiovascular Interventions, Auctores Publishing LLC. The peer review process of the journal of Clinical Cardiology and Cardiovascular Interventions was excellent and fast, as was the support of the editorial office and the quality of the journal. Kind regards Walter F. Riesen Prof. Dr. Dr. h.c. Walter F. Riesen.

Dear Ashley Rosa, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews, Auctores Publishing LLC. Thank you for publishing our article, Exploring Clozapine's Efficacy in Managing Aggression: A Multiple Single-Case Study in Forensic Psychiatry in the international journal of clinical case reports and reviews. We found the peer review process very professional and efficient. The comments were constructive, and the whole process was efficient. On behalf of the co-authors, I would like to thank you for publishing this article. With regards, Dr. Jelle R. Lettinga.

Dear Clarissa Eric, Editorial Coordinator, Journal of Clinical Case Reports and Studies, I would like to express my deep admiration for the exceptional professionalism demonstrated by your journal. I am thoroughly impressed by the speed of the editorial process, the substantive and insightful reviews, and the meticulous preparation of the manuscript for publication. Additionally, I greatly appreciate the courteous and immediate responses from your editorial office to all my inquiries. Best Regards, Dariusz Ziora

Dear Chrystine Mejia, Editorial Coordinator, Journal of Neurodegeneration and Neurorehabilitation, Auctores Publishing LLC, We would like to thank the editorial team for the smooth and high-quality communication leading up to the publication of our article in the Journal of Neurodegeneration and Neurorehabilitation. The reviewers have extensive knowledge in the field, and their relevant questions helped to add value to our publication. Kind regards, Dr. Ravi Shrivastava.

Dear Clarissa Eric, Editorial Coordinator, Journal of Clinical Case Reports and Studies, Auctores Publishing LLC, USA Office: +1-(302)-520-2644. I would like to express my sincere appreciation for the efficient and professional handling of my case report by the ‘Journal of Clinical Case Reports and Studies’. The peer review process was not only fast but also highly constructive—the reviewers’ comments were clear, relevant, and greatly helped me improve the quality and clarity of my manuscript. I also received excellent support from the editorial office throughout the process. Communication was smooth and timely, and I felt well guided at every stage, from submission to publication. The overall quality and rigor of the journal are truly commendable. I am pleased to have published my work with Journal of Clinical Case Reports and Studies, and I look forward to future opportunities for collaboration. Sincerely, Aline Tollet, UCLouvain.

Dear Ms. Mayra Duenas, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews. “The International Journal of Clinical Case Reports and Reviews represented the “ideal house” to share with the research community a first experience with the use of the Simeox device for speech rehabilitation. High scientific reputation and attractive website communication were first determinants for the selection of this Journal, and the following submission process exceeded expectations: fast but highly professional peer review, great support by the editorial office, elegant graphic layout. Exactly what a dynamic research team - also composed by allied professionals - needs!" From, Chiara Beccaluva, PT - Italy.

Dear Maria Emerson, Editorial Coordinator, we have deeply appreciated the professionalism demonstrated by the International Journal of Clinical Case Reports and Reviews. The reviewers have extensive knowledge of our field and have been very efficient and fast in supporting the process. I am really looking forward to further collaboration. Thanks. Best regards, Dr. Claudio Ligresti
Dear Chrystine Mejia, Editorial Coordinator, Journal of Neurodegeneration and Neurorehabilitation. “The peer review process was efficient and constructive, and the editorial office provided excellent communication and support throughout. The journal ensures scientific rigor and high editorial standards, while also offering a smooth and timely publication process. We sincerely appreciate the work of the editorial team in facilitating the dissemination of innovative approaches such as the Bonori Method.” Best regards, Dr. Matteo Bonori.

I recommend without hesitation submitting relevant papers on medical decision making to the International Journal of Clinical Case Reports and Reviews. I am very grateful to the editorial staff. Maria Emerson was a pleasure to communicate with. The time from submission to publication was an extremely short 3 weeks. The editorial staff submitted the paper to three reviewers. Two of the reviewers commented positively on the value of publishing the paper. The editorial staff quickly recognized the third reviewer’s comments as an unjust attempt to reject the paper. I revised the paper as recommended by the first two reviewers.

Dear Maria Emerson, Editorial Coordinator, Journal of Clinical Research and Reports. Thank you for publishing our case report: "Clinical Case of Effective Fetal Stem Cells Treatment in a Patient with Autism Spectrum Disorder" within the "Journal of Clinical Research and Reports" being submitted by the team of EmCell doctors from Kyiv, Ukraine. We much appreciate a professional and transparent peer-review process from Auctores. All research Doctors are so grateful to your Editorial Office and Auctores Publishing support! I amiably wish our article publication maintained a top quality of your International Scientific Journal. My best wishes for a prosperity of the Journal of Clinical Research and Reports. Hope our scientific relationship and cooperation will remain long lasting. Thank you very much indeed. Kind regards, Dr. Andriy Sinelnyk Cell Therapy Center EmCell

Dear Editorial Team, Clinical Cardiology and Cardiovascular Interventions. It was truly a rewarding experience to work with the journal “Clinical Cardiology and Cardiovascular Interventions”. The peer review process was insightful and encouraging, helping us refine our work to a higher standard. The editorial office offered exceptional support with prompt and thoughtful communication. I highly value the journal’s role in promoting scientific advancement and am honored to be part of it. Best regards, Meng-Jou Lee, MD, Department of Anesthesiology, National Taiwan University Hospital.

Dear Editorial Team, Journal-Clinical Cardiology and Cardiovascular Interventions, “Publishing my article with Clinical Cardiology and Cardiovascular Interventions has been a highly positive experience. The peer-review process was rigorous yet supportive, offering valuable feedback that strengthened my work. The editorial team demonstrated exceptional professionalism, prompt communication, and a genuine commitment to maintaining the highest scientific standards. I am very pleased with the publication quality and proud to be associated with such a reputable journal.” Warm regards, Dr. Mahmoud Kamal Moustafa Ahmed

Dear Maria Emerson, Editorial Coordinator of ‘International Journal of Clinical Case Reports and Reviews’, I appreciate the opportunity to publish my article with your journal. The editorial office provided clear communication during the submission and review process, and I found the overall experience professional and constructive. Best regards, Elena Salvatore.

Dear Mayra Duenas, Editorial Coordinator of ‘International Journal of Clinical Case Reports and Reviews Herewith I confirm an optimal peer review process and a great support of the editorial office of the present journal
Dear Editorial Team, Clinical Cardiology and Cardiovascular Interventions. I am really grateful for the peers review; their feedback gave me the opportunity to reflect on the message and impact of my work and to ameliorate the article. The editors did a great job in addition by encouraging me to continue with the process of publishing.

Dear Cecilia Lilly, Editorial Coordinator, Endocrinology and Disorders, Thank you so much for your quick response regarding reviewing and all process till publishing our manuscript entitled: Prevalence of Pre-Diabetes and its Associated Risk Factors Among Nile College Students, Sudan. Best regards, Dr Mamoun Magzoub.

International Journal of Clinical Case Reports and Reviews is a high quality journal that has a clear and concise submission process. The peer review process was comprehensive and constructive. Support from the editorial office was excellent, since the administrative staff were responsive. The journal provides a fast and timely publication timeline.

Dear Maria Emerson, Editorial Coordinator of International Journal of Clinical Case Reports and Reviews, What distinguishes International Journal of Clinical Case Report and Review is not only the scientific rigor of its publications, but the intellectual climate in which research is evaluated. The submission process is refreshingly free of unnecessary formal barriers and bureaucratic rituals that often complicate academic publishing without adding real value. The peer-review system is demanding yet constructive, guided by genuine scientific dialogue rather than hierarchical or authoritarian attitudes. Reviewers act as collaborators in improving the manuscript, not as gatekeepers imposing arbitrary standards. This journal offers a rare balance: high methodological standards combined with a respectful, transparent, and supportive editorial approach. In an era where publishing can feel more burdensome than research itself, this platform restores the original purpose of peer review — to refine ideas, not to obstruct them Prof. Perlat Kapisyzi, FCCP PULMONOLOGIST AND THORACIC IMAGING.

Dear Grace Pierce, International Journal of Clinical Case Reports and Reviews I appreciate the opportunity to review for Auctore Journal, as the overall editorial process was smooth, transparent and professionally managed. This journal maintains high scientific standards and ensures timely communications with authors, which is truly commendable. I would like to express my special thanks to editor Grace Pierce for his constant guidance, promt responses, and supportive coordination throughout the review process. I am also greatful to Eleanor Bailey from the finance department for her clear communication and efficient handling of all administrative matters. Overall, my experience with Auctore Journal has been highly positive and rewarding. Best regards, Sabita sinha

Dear Mayra Duenas, Editorial Coordinator of the journal IJCCR, I write here a little on my experience as an author submitting to the International Journal of Clinical Case Reports and Reviews (IJCCR). This was my first submission to IJCCR and my manuscript was inherently an outsider’s effort. It attempted to broadly identify and then make some sense of life’s under-appreciated mysteries. I initially had responded to a request for possible submissions. I then contacted IJCCR with a tentative topic for a manuscript. They quickly got back with an approval for the submission, but with a particular requirement that it be medically relevant. I then put together a manuscript and submitted it. After the usual back-and-forth over forms and formality, the manuscript was sent off for reviews. Within 2 weeks I got back 4 reviews which were both helpful and also surprising. Surprising in that the topic was somewhat foreign to medical literature. My subsequent updates in response to the reviewer comments went smoothly and in short order I had a series of proofs to evaluate. All in all, the whole publication process seemed outstanding. It was both helpful in terms of the paper’s content and also in terms of its efficient and friendly communications. Thank you all very much. Sincerely, Ted Christopher, Rochester, NY.
