AUCTORES
Globalize your Research
Research Article | DOI: https://doi.org/10.31579/2639-4162/176
1Institute for IT Innovation and Smart Health, Mississippi, USA.
2Institute for Systems Engineering Research, Mississippi State University, Mississippi, USA.
*Corresponding Author: Cheryl Ann Alexander, Institute for IT Innovation and Smart Health, Mississippi, USA.
Citation: Cheryl A. Alexander and Lidong Wang, (2024), Asset Security and Asset Management: Cybersecurity Case Study of a Large Medical Center, J. General Medicine and Clinical Practice, 7(9); DOI:10.31579/2639-4162/176
Copyright: © 2024, Cheryl Ann Alexander. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Received: 15 April 2024 | Accepted: 09 May 2024 | Published: 15 May 2024
Keywords: cybersecurity; data governance; data policy; asset management; asset classifications
Asset management is a crucial process for every enterprise. Asset classification is necessary to determine the risk factors for cybercrimes and the safety of essential equipment, medications, hardware and software, and data. Identification of information and classifying data and the associated equipment can alleviate surprise attacks and prevent criminals from absconding with data or other data-related equipment. There are numerous levels of classification, and it is critical to look at vulnerabilities and what information or data needs the most protection. Data policy, data governance, and data standards protect data and should be considered when classifying the data. This paper discusses developing an asset security and management program for a mid-level medical center. Data is an essential asset in any medical center and the identification of hardware and software components and application patch levels that can be categorized are key elements of cybersecurity.
Information management across industries has significantly changed as critical blind spots have become increasingly more difficult to find and repair for professionals, and tools for protecting data have failed to meet the challenges of defending that data. As companies continue to upgrade their digital operations, they leave themselves more vulnerable to attacks. Healthcare data continues to be more valuable than financial or personal data. As organizations continue to participate in digital transformations, scaling up their organization, and integrating the Internet of Things (IoT) or Internet of Medical Things (IoMT), the threat window for security issues widens and becomes more ominous; many cybersecurity teams now struggle to stay abreast of threats. In this age of digital growth, cybersecurity professionals must now consider data as the primary asset and analyze threats across systems, devices, and the cloud. Enterprises must maintain a strong and robust asset management program, become more resilient to cyberattacks, and generate business value by creating an advanced and strong cybersecurity program that protects their data from cyberattacks (Mishra & Gochhait, 2023).
Data as an Asset
Data is the primary asset in any medical center. Having a robust cybersecurity program is essential for protecting not only the patient data but also staff and data significant for the operation of the medical center such as financial or staff employee records. However, data must be classified or organized into tiers or classes so that security controls can be determined that manage and preserve the data against theft, unauthorized access (i.e., the most common data threat in the medical center), and improper retention or unsafe destruction of data such as throwing items which have not been deidentified into a garbage can (Warsinske et al., 2019). Once a data categorization policy and procedures have been developed and implemented, the medical center can then develop specific cybersecurity protocols based on the level of importance or sensitivity. For example, data in the medical center is classified as sensitive, confidential, private, public, or proprietary (i.e., patient data that has limited use outside of the facility such as billing data or patient data for research). Once data classification is finished, the medical center can categorize data, achieving two important functions: a) to establish risk tolerance and b) it assigns the value the organization places on the data (Warsinske et al., 2019). Customarily, asset management for information technology (IT) describes a set of practices in financial, inventory, and the lifecycle of an asset. IT assets are any devices used for business purposes (Burke, 2020). Medical centers are adopting the use of cloud technology, artificial intelligence (AI), IoMT, and other digital resources to protect against cyber threats and keep data safe. Web services, cell phones, biometrics such as fingerprint scanners, barcoding, etc., and other encrypted personal devices are just a few of the assets that a medical center must protect.
Cybersecurity for Asset Management
Asset management becomes vitally important the larger the organization. How the organization operates is another contributing factor to how strong a cybersecurity program must be. Most often, cybersecurity professionals working in these organizations suggest that cybersecurity programs be robust and that management continues to upgrade based on current threats (Norris et al., 2021). Cybersecurity has certain social, economic, and political effects that have only increased as medical centers have to worry about patient data, regulatory laws, privacy standards, and others. This should not be surprising as the digital world grows and data becomes not only richer, but more extended. However, some gaps still exist such as gaps in the knowledge base and an overall lack of clarity (i.e., noisy data, unstructured data, etc.). But at the same time, practitioners, cybersecurity professionals, and researchers must begin to think of data as an asset (Serrano, 2023). Asset management has been around for many years. Organizations must learn to preserve identify and categorize data to protect patients, staff, practitioners, and researchers. Organizations need to preserve data for legal or forensic reasons or privacy and to protect intellectual property. The steps necessary to build data retention and protect the data that is crucial to an enterprise begin with asset management and the individual or team designated to protect the data (Warsinske et al., 2019).
Network Components and Included Assets
Assets in Charleston Regional Medical Center include all the hardware and software in the three layers, APIs, and the Control Data Plane Interface demonstrated in Figure 1. Various software in the application layer is used for access controls, e-health, telehealth, patient monitoring, AI-driven applications, Big Data analytics, intrusion/attack detection, etc. The controllers in the control layer monitor, control, and manage the hardware in the infrastructure layer. The intelligent or smart assets provide enhanced functionality to the entire medical center. Improved functionality, including enhanced patient care, and in some cases, personalized medicine is enabled by Big Data analytics, AI, mobile apps, IoMT, etc. Superior patient care, personalized medicine in some cases, and reduced energy consumption are a result of a careful asset management program by the medical center. The main uniqueness is that technology and intangible assets can be standardized and subject to ubiquitous regulatory and ethical standards, while land, buildings, machines, etc. are subject to different standards and regulatory bodies (Serrano, 2023). In the infrastructure layer, assets include network devices, servers, storage devices, computing hardware, Internet of Things (IoT), Internet of Medical Things (IoMT), and machines such as barcoding scanners, fingerprint scanners, radio frequency identification (RFID) scanners, etc. IoMT can include medical devices, nurses’ stations, etc. IoT, IoMT, barcoding scanners, and RFID scanners are used for data capture; fingerprint scanners are used for verification based on captured persons’ fingerprints (patterns).
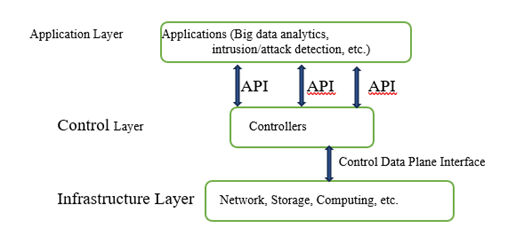
Figure 1. Network Components in the Medical Center
Asset Classification in the Medical Center
Table 1 shows information asset classifications in the Medical Center. Significant systems with a network or sensitive data, such as electronic medical records (EMRs), electronic health records (EHRs), or Protected health information (PHI) are described in the table. The significance level (high, medium, or low) for each asset is determined based on confidentiality, integrity, and availability.
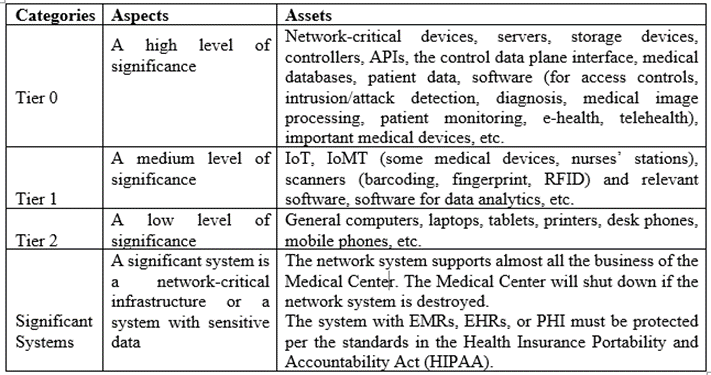
Table 1. Classifications of Information Assets in the Medical Center
A chief executive officer (CEO), Board of Directors, Medical Board, or other authorized delegates have formal ownership responsibility. For example, a data owner is the person or group of individuals responsible and accountable for the data. A data owner sets rules for data utilization and data protection. A data policy outlines the guidelines for using, collecting, sharing, storing data, and destroying any data once it is no longer needed. An information asset security management (IASM) policy provides high-level, relevant guidance for the acceptable use of data, legal and regulatory considerations, and the roles and responsibilities of data users. The goal of data governance is to stop data-related problems before they arise (Warsinske et al., 2019). A data governance committee is created to ensure that data is protected under the statute, contract, or compliance/regulatory bodies. Table 2 shows the owners of assets, data policy, IASM policy, and data governance in the Medical Center. In Table 2, the owner of an asset can be the CEO of the Medical Center, the Business Manager, the Manager of the Information Security Department (ISD) in the Medical Center, or other authorized staff.
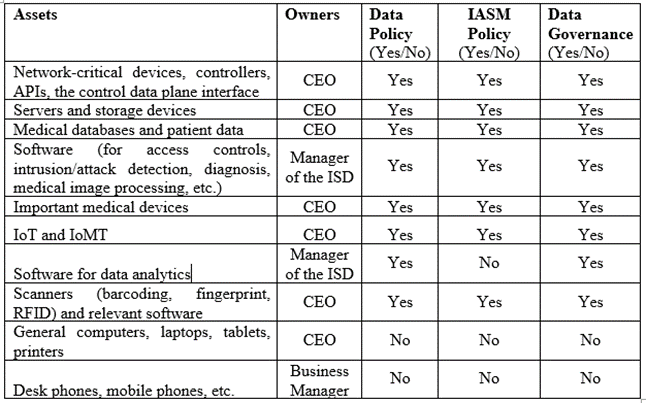
Table 2. Owners of Assets, Data Policy, IASM Policy, and Data Governance
Software applications in the Medical Center mainly include access controls, intrusion/attack detection systems, diagnosis, medical image processing, data analytics, and scanners (barcoding, fingerprint, RFID). Software asset management includes vulnerability scanning and application patching for operating systems, third-party applications, and firmware. Patch management is a significant part of keeping software up-to-date and secure (Warsinske et al., 2019). Table 3 shows the inventory of software applications, the current list of known vulnerabilities, prioritization of each vulnerability by risk level (high, medium, and low), actions to patch or apply alternative controls, and application patch levels (high, medium, and low from software vendor if applicable). There are three main manifestations of access control vulnerabilities: vertical (sensitive functionalities), horizontal (also called lateral: resources), and context-dependent (resources and functionalities based on the application’s context and user activity) (Zhong, 2023). There are different vulnerabilities in other software applications (see Table 3).
Actions to Patch or Apply Alternative Controls, and Application Patch Levels
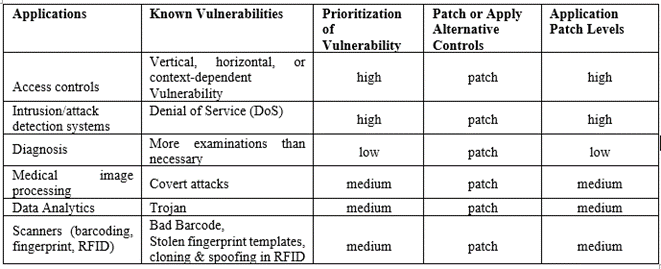
Table 3. Inventory of Software Applications, Vulnerabilities, and Their Prioritization,
Actions to Patch or Apply Alternative Controls, and Application Patch Levels
Asset security is a fundamental process for an enterprise. By managing the assets, through identification and categorization, the enterprise can maintain asset security very well and identify any threats to the assets. For Charleston Medical Center, a mid-level facility, asset security involves data and identification of assets related to data security. For example, data mining equipment, servers, MIoT, IoT, the intranet, etc. The first task for asset management is to identify and organize the assets. RFID equipment, barcodes, templates, machine learning equipment, hardware, and software are all assets that are key to security. Some examples of cybersecurity breaches include staff who use electronic health records to keep up with family, neighbors, etc. Keeping the data secure and protected from cybercriminals is a crucial job for the IT department. It is also important to have cybersecurity on patch levels compliance—too high or too level can become an entrance for many crimes there.
The authors thank Technology & Healthcare Solutions, Mississippi, USA for its support.
There is no conflict of interest.
Clearly Auctoresonline and particularly Psychology and Mental Health Care Journal is dedicated to improving health care services for individuals and populations. The editorial boards' ability to efficiently recognize and share the global importance of health literacy with a variety of stakeholders. Auctoresonline publishing platform can be used to facilitate of optimal client-based services and should be added to health care professionals' repertoire of evidence-based health care resources.

Journal of Clinical Cardiology and Cardiovascular Intervention The submission and review process was adequate. However I think that the publication total value should have been enlightened in early fases. Thank you for all.

Journal of Women Health Care and Issues By the present mail, I want to say thank to you and tour colleagues for facilitating my published article. Specially thank you for the peer review process, support from the editorial office. I appreciate positively the quality of your journal.
Journal of Clinical Research and Reports I would be very delighted to submit my testimonial regarding the reviewer board and the editorial office. The reviewer board were accurate and helpful regarding any modifications for my manuscript. And the editorial office were very helpful and supportive in contacting and monitoring with any update and offering help. It was my pleasure to contribute with your promising Journal and I am looking forward for more collaboration.

We would like to thank the Journal of Thoracic Disease and Cardiothoracic Surgery because of the services they provided us for our articles. The peer-review process was done in a very excellent time manner, and the opinions of the reviewers helped us to improve our manuscript further. The editorial office had an outstanding correspondence with us and guided us in many ways. During a hard time of the pandemic that is affecting every one of us tremendously, the editorial office helped us make everything easier for publishing scientific work. Hope for a more scientific relationship with your Journal.

The peer-review process which consisted high quality queries on the paper. I did answer six reviewers’ questions and comments before the paper was accepted. The support from the editorial office is excellent.

Journal of Neuroscience and Neurological Surgery. I had the experience of publishing a research article recently. The whole process was simple from submission to publication. The reviewers made specific and valuable recommendations and corrections that improved the quality of my publication. I strongly recommend this Journal.

Dr. Katarzyna Byczkowska My testimonial covering: "The peer review process is quick and effective. The support from the editorial office is very professional and friendly. Quality of the Clinical Cardiology and Cardiovascular Interventions is scientific and publishes ground-breaking research on cardiology that is useful for other professionals in the field.

Thank you most sincerely, with regard to the support you have given in relation to the reviewing process and the processing of my article entitled "Large Cell Neuroendocrine Carcinoma of The Prostate Gland: A Review and Update" for publication in your esteemed Journal, Journal of Cancer Research and Cellular Therapeutics". The editorial team has been very supportive.

Testimony of Journal of Clinical Otorhinolaryngology: work with your Reviews has been a educational and constructive experience. The editorial office were very helpful and supportive. It was a pleasure to contribute to your Journal.

Dr. Bernard Terkimbi Utoo, I am happy to publish my scientific work in Journal of Women Health Care and Issues (JWHCI). The manuscript submission was seamless and peer review process was top notch. I was amazed that 4 reviewers worked on the manuscript which made it a highly technical, standard and excellent quality paper. I appreciate the format and consideration for the APC as well as the speed of publication. It is my pleasure to continue with this scientific relationship with the esteem JWHCI.

This is an acknowledgment for peer reviewers, editorial board of Journal of Clinical Research and Reports. They show a lot of consideration for us as publishers for our research article “Evaluation of the different factors associated with side effects of COVID-19 vaccination on medical students, Mutah university, Al-Karak, Jordan”, in a very professional and easy way. This journal is one of outstanding medical journal.
Dear Hao Jiang, to Journal of Nutrition and Food Processing We greatly appreciate the efficient, professional and rapid processing of our paper by your team. If there is anything else we should do, please do not hesitate to let us know. On behalf of my co-authors, we would like to express our great appreciation to editor and reviewers.

As an author who has recently published in the journal "Brain and Neurological Disorders". I am delighted to provide a testimonial on the peer review process, editorial office support, and the overall quality of the journal. The peer review process at Brain and Neurological Disorders is rigorous and meticulous, ensuring that only high-quality, evidence-based research is published. The reviewers are experts in their fields, and their comments and suggestions were constructive and helped improve the quality of my manuscript. The review process was timely and efficient, with clear communication from the editorial office at each stage. The support from the editorial office was exceptional throughout the entire process. The editorial staff was responsive, professional, and always willing to help. They provided valuable guidance on formatting, structure, and ethical considerations, making the submission process seamless. Moreover, they kept me informed about the status of my manuscript and provided timely updates, which made the process less stressful. The journal Brain and Neurological Disorders is of the highest quality, with a strong focus on publishing cutting-edge research in the field of neurology. The articles published in this journal are well-researched, rigorously peer-reviewed, and written by experts in the field. The journal maintains high standards, ensuring that readers are provided with the most up-to-date and reliable information on brain and neurological disorders. In conclusion, I had a wonderful experience publishing in Brain and Neurological Disorders. The peer review process was thorough, the editorial office provided exceptional support, and the journal's quality is second to none. I would highly recommend this journal to any researcher working in the field of neurology and brain disorders.

Dear Agrippa Hilda, Journal of Neuroscience and Neurological Surgery, Editorial Coordinator, I trust this message finds you well. I want to extend my appreciation for considering my article for publication in your esteemed journal. I am pleased to provide a testimonial regarding the peer review process and the support received from your editorial office. The peer review process for my paper was carried out in a highly professional and thorough manner. The feedback and comments provided by the authors were constructive and very useful in improving the quality of the manuscript. This rigorous assessment process undoubtedly contributes to the high standards maintained by your journal.

International Journal of Clinical Case Reports and Reviews. I strongly recommend to consider submitting your work to this high-quality journal. The support and availability of the Editorial staff is outstanding and the review process was both efficient and rigorous.

Thank you very much for publishing my Research Article titled “Comparing Treatment Outcome Of Allergic Rhinitis Patients After Using Fluticasone Nasal Spray And Nasal Douching" in the Journal of Clinical Otorhinolaryngology. As Medical Professionals we are immensely benefited from study of various informative Articles and Papers published in this high quality Journal. I look forward to enriching my knowledge by regular study of the Journal and contribute my future work in the field of ENT through the Journal for use by the medical fraternity. The support from the Editorial office was excellent and very prompt. I also welcome the comments received from the readers of my Research Article.

Dear Erica Kelsey, Editorial Coordinator of Cancer Research and Cellular Therapeutics Our team is very satisfied with the processing of our paper by your journal. That was fast, efficient, rigorous, but without unnecessary complications. We appreciated the very short time between the submission of the paper and its publication on line on your site.

I am very glad to say that the peer review process is very successful and fast and support from the Editorial Office. Therefore, I would like to continue our scientific relationship for a long time. And I especially thank you for your kindly attention towards my article. Have a good day!

"We recently published an article entitled “Influence of beta-Cyclodextrins upon the Degradation of Carbofuran Derivatives under Alkaline Conditions" in the Journal of “Pesticides and Biofertilizers” to show that the cyclodextrins protect the carbamates increasing their half-life time in the presence of basic conditions This will be very helpful to understand carbofuran behaviour in the analytical, agro-environmental and food areas. We greatly appreciated the interaction with the editor and the editorial team; we were particularly well accompanied during the course of the revision process, since all various steps towards publication were short and without delay".

I would like to express my gratitude towards you process of article review and submission. I found this to be very fair and expedient. Your follow up has been excellent. I have many publications in national and international journal and your process has been one of the best so far. Keep up the great work.

We are grateful for this opportunity to provide a glowing recommendation to the Journal of Psychiatry and Psychotherapy. We found that the editorial team were very supportive, helpful, kept us abreast of timelines and over all very professional in nature. The peer review process was rigorous, efficient and constructive that really enhanced our article submission. The experience with this journal remains one of our best ever and we look forward to providing future submissions in the near future.

I am very pleased to serve as EBM of the journal, I hope many years of my experience in stem cells can help the journal from one way or another. As we know, stem cells hold great potential for regenerative medicine, which are mostly used to promote the repair response of diseased, dysfunctional or injured tissue using stem cells or their derivatives. I think Stem Cell Research and Therapeutics International is a great platform to publish and share the understanding towards the biology and translational or clinical application of stem cells.

I would like to give my testimony in the support I have got by the peer review process and to support the editorial office where they were of asset to support young author like me to be encouraged to publish their work in your respected journal and globalize and share knowledge across the globe. I really give my great gratitude to your journal and the peer review including the editorial office.

I am delighted to publish our manuscript entitled "A Perspective on Cocaine Induced Stroke - Its Mechanisms and Management" in the Journal of Neuroscience and Neurological Surgery. The peer review process, support from the editorial office, and quality of the journal are excellent. The manuscripts published are of high quality and of excellent scientific value. I recommend this journal very much to colleagues.

Dr.Tania Muñoz, My experience as researcher and author of a review article in The Journal Clinical Cardiology and Interventions has been very enriching and stimulating. The editorial team is excellent, performs its work with absolute responsibility and delivery. They are proactive, dynamic and receptive to all proposals. Supporting at all times the vast universe of authors who choose them as an option for publication. The team of review specialists, members of the editorial board, are brilliant professionals, with remarkable performance in medical research and scientific methodology. Together they form a frontline team that consolidates the JCCI as a magnificent option for the publication and review of high-level medical articles and broad collective interest. I am honored to be able to share my review article and open to receive all your comments.

“The peer review process of JPMHC is quick and effective. Authors are benefited by good and professional reviewers with huge experience in the field of psychology and mental health. The support from the editorial office is very professional. People to contact to are friendly and happy to help and assist any query authors might have. Quality of the Journal is scientific and publishes ground-breaking research on mental health that is useful for other professionals in the field”.

Dear editorial department: On behalf of our team, I hereby certify the reliability and superiority of the International Journal of Clinical Case Reports and Reviews in the peer review process, editorial support, and journal quality. Firstly, the peer review process of the International Journal of Clinical Case Reports and Reviews is rigorous, fair, transparent, fast, and of high quality. The editorial department invites experts from relevant fields as anonymous reviewers to review all submitted manuscripts. These experts have rich academic backgrounds and experience, and can accurately evaluate the academic quality, originality, and suitability of manuscripts. The editorial department is committed to ensuring the rigor of the peer review process, while also making every effort to ensure a fast review cycle to meet the needs of authors and the academic community. Secondly, the editorial team of the International Journal of Clinical Case Reports and Reviews is composed of a group of senior scholars and professionals with rich experience and professional knowledge in related fields. The editorial department is committed to assisting authors in improving their manuscripts, ensuring their academic accuracy, clarity, and completeness. Editors actively collaborate with authors, providing useful suggestions and feedback to promote the improvement and development of the manuscript. We believe that the support of the editorial department is one of the key factors in ensuring the quality of the journal. Finally, the International Journal of Clinical Case Reports and Reviews is renowned for its high- quality articles and strict academic standards. The editorial department is committed to publishing innovative and academically valuable research results to promote the development and progress of related fields. The International Journal of Clinical Case Reports and Reviews is reasonably priced and ensures excellent service and quality ratio, allowing authors to obtain high-level academic publishing opportunities in an affordable manner. I hereby solemnly declare that the International Journal of Clinical Case Reports and Reviews has a high level of credibility and superiority in terms of peer review process, editorial support, reasonable fees, and journal quality. Sincerely, Rui Tao.

Clinical Cardiology and Cardiovascular Interventions I testity the covering of the peer review process, support from the editorial office, and quality of the journal.

Clinical Cardiology and Cardiovascular Interventions, we deeply appreciate the interest shown in our work and its publication. It has been a true pleasure to collaborate with you. The peer review process, as well as the support provided by the editorial office, have been exceptional, and the quality of the journal is very high, which was a determining factor in our decision to publish with you.
The peer reviewers process is quick and effective, the supports from editorial office is excellent, the quality of journal is high. I would like to collabroate with Internatioanl journal of Clinical Case Reports and Reviews journal clinically in the future time.

Clinical Cardiology and Cardiovascular Interventions, I would like to express my sincerest gratitude for the trust placed in our team for the publication in your journal. It has been a true pleasure to collaborate with you on this project. I am pleased to inform you that both the peer review process and the attention from the editorial coordination have been excellent. Your team has worked with dedication and professionalism to ensure that your publication meets the highest standards of quality. We are confident that this collaboration will result in mutual success, and we are eager to see the fruits of this shared effort.

Dear Dr. Jessica Magne, Editorial Coordinator 0f Clinical Cardiology and Cardiovascular Interventions, I hope this message finds you well. I want to express my utmost gratitude for your excellent work and for the dedication and speed in the publication process of my article titled "Navigating Innovation: Qualitative Insights on Using Technology for Health Education in Acute Coronary Syndrome Patients." I am very satisfied with the peer review process, the support from the editorial office, and the quality of the journal. I hope we can maintain our scientific relationship in the long term.
Dear Monica Gissare, - Editorial Coordinator of Nutrition and Food Processing. ¨My testimony with you is truly professional, with a positive response regarding the follow-up of the article and its review, you took into account my qualities and the importance of the topic¨.

Dear Dr. Jessica Magne, Editorial Coordinator 0f Clinical Cardiology and Cardiovascular Interventions, The review process for the article “The Handling of Anti-aggregants and Anticoagulants in the Oncologic Heart Patient Submitted to Surgery” was extremely rigorous and detailed. From the initial submission to the final acceptance, the editorial team at the “Journal of Clinical Cardiology and Cardiovascular Interventions” demonstrated a high level of professionalism and dedication. The reviewers provided constructive and detailed feedback, which was essential for improving the quality of our work. Communication was always clear and efficient, ensuring that all our questions were promptly addressed. The quality of the “Journal of Clinical Cardiology and Cardiovascular Interventions” is undeniable. It is a peer-reviewed, open-access publication dedicated exclusively to disseminating high-quality research in the field of clinical cardiology and cardiovascular interventions. The journal's impact factor is currently under evaluation, and it is indexed in reputable databases, which further reinforces its credibility and relevance in the scientific field. I highly recommend this journal to researchers looking for a reputable platform to publish their studies.

Dear Editorial Coordinator of the Journal of Nutrition and Food Processing! "I would like to thank the Journal of Nutrition and Food Processing for including and publishing my article. The peer review process was very quick, movement and precise. The Editorial Board has done an extremely conscientious job with much help, valuable comments and advices. I find the journal very valuable from a professional point of view, thank you very much for allowing me to be part of it and I would like to participate in the future!”

Dealing with The Journal of Neurology and Neurological Surgery was very smooth and comprehensive. The office staff took time to address my needs and the response from editors and the office was prompt and fair. I certainly hope to publish with this journal again.Their professionalism is apparent and more than satisfactory. Susan Weiner

My Testimonial Covering as fellowing: Lin-Show Chin. The peer reviewers process is quick and effective, the supports from editorial office is excellent, the quality of journal is high. I would like to collabroate with Internatioanl journal of Clinical Case Reports and Reviews.

My experience publishing in Psychology and Mental Health Care was exceptional. The peer review process was rigorous and constructive, with reviewers providing valuable insights that helped enhance the quality of our work. The editorial team was highly supportive and responsive, making the submission process smooth and efficient. The journal's commitment to high standards and academic rigor makes it a respected platform for quality research. I am grateful for the opportunity to publish in such a reputable journal.
My experience publishing in International Journal of Clinical Case Reports and Reviews was exceptional. I Come forth to Provide a Testimonial Covering the Peer Review Process and the editorial office for the Professional and Impartial Evaluation of the Manuscript.

I would like to offer my testimony in the support. I have received through the peer review process and support the editorial office where they are to support young authors like me, encourage them to publish their work in your esteemed journals, and globalize and share knowledge globally. I really appreciate your journal, peer review, and editorial office.
Dear Agrippa Hilda- Editorial Coordinator of Journal of Neuroscience and Neurological Surgery, "The peer review process was very quick and of high quality, which can also be seen in the articles in the journal. The collaboration with the editorial office was very good."

I would like to express my sincere gratitude for the support and efficiency provided by the editorial office throughout the publication process of my article, “Delayed Vulvar Metastases from Rectal Carcinoma: A Case Report.” I greatly appreciate the assistance and guidance I received from your team, which made the entire process smooth and efficient. The peer review process was thorough and constructive, contributing to the overall quality of the final article. I am very grateful for the high level of professionalism and commitment shown by the editorial staff, and I look forward to maintaining a long-term collaboration with the International Journal of Clinical Case Reports and Reviews.
To Dear Erin Aust, I would like to express my heartfelt appreciation for the opportunity to have my work published in this esteemed journal. The entire publication process was smooth and well-organized, and I am extremely satisfied with the final result. The Editorial Team demonstrated the utmost professionalism, providing prompt and insightful feedback throughout the review process. Their clear communication and constructive suggestions were invaluable in enhancing my manuscript, and their meticulous attention to detail and dedication to quality are truly commendable. Additionally, the support from the Editorial Office was exceptional. From the initial submission to the final publication, I was guided through every step of the process with great care and professionalism. The team's responsiveness and assistance made the entire experience both easy and stress-free. I am also deeply impressed by the quality and reputation of the journal. It is an honor to have my research featured in such a respected publication, and I am confident that it will make a meaningful contribution to the field.

"I am grateful for the opportunity of contributing to [International Journal of Clinical Case Reports and Reviews] and for the rigorous review process that enhances the quality of research published in your esteemed journal. I sincerely appreciate the time and effort of your team who have dedicatedly helped me in improvising changes and modifying my manuscript. The insightful comments and constructive feedback provided have been invaluable in refining and strengthening my work".

I thank the ‘Journal of Clinical Research and Reports’ for accepting this article for publication. This is a rigorously peer reviewed journal which is on all major global scientific data bases. I note the review process was prompt, thorough and professionally critical. It gave us an insight into a number of important scientific/statistical issues. The review prompted us to review the relevant literature again and look at the limitations of the study. The peer reviewers were open, clear in the instructions and the editorial team was very prompt in their communication. This journal certainly publishes quality research articles. I would recommend the journal for any future publications.

Dear Jessica Magne, with gratitude for the joint work. Fast process of receiving and processing the submitted scientific materials in “Clinical Cardiology and Cardiovascular Interventions”. High level of competence of the editors with clear and correct recommendations and ideas for enriching the article.

We found the peer review process quick and positive in its input. The support from the editorial officer has been very agile, always with the intention of improving the article and taking into account our subsequent corrections.

My article, titled 'No Way Out of the Smartphone Epidemic Without Considering the Insights of Brain Research,' has been republished in the International Journal of Clinical Case Reports and Reviews. The review process was seamless and professional, with the editors being both friendly and supportive. I am deeply grateful for their efforts.
To Dear Erin Aust – Editorial Coordinator of Journal of General Medicine and Clinical Practice! I declare that I am absolutely satisfied with your work carried out with great competence in following the manuscript during the various stages from its receipt, during the revision process to the final acceptance for publication. Thank Prof. Elvira Farina

Dear Jessica, and the super professional team of the ‘Clinical Cardiology and Cardiovascular Interventions’ I am sincerely grateful to the coordinated work of the journal team for the no problem with the submission of my manuscript: “Cardiometabolic Disorders in A Pregnant Woman with Severe Preeclampsia on the Background of Morbid Obesity (Case Report).” The review process by 5 experts was fast, and the comments were professional, which made it more specific and academic, and the process of publication and presentation of the article was excellent. I recommend that my colleagues publish articles in this journal, and I am interested in further scientific cooperation. Sincerely and best wishes, Dr. Oleg Golyanovskiy.

Dear Ashley Rosa, Editorial Coordinator of the journal - Psychology and Mental Health Care. " The process of obtaining publication of my article in the Psychology and Mental Health Journal was positive in all areas. The peer review process resulted in a number of valuable comments, the editorial process was collaborative and timely, and the quality of this journal has been quickly noticed, resulting in alternative journals contacting me to publish with them." Warm regards, Susan Anne Smith, PhD. Australian Breastfeeding Association.

Dear Jessica Magne, Editorial Coordinator, Clinical Cardiology and Cardiovascular Interventions, Auctores Publishing LLC. I appreciate the journal (JCCI) editorial office support, the entire team leads were always ready to help, not only on technical front but also on thorough process. Also, I should thank dear reviewers’ attention to detail and creative approach to teach me and bring new insights by their comments. Surely, more discussions and introduction of other hemodynamic devices would provide better prevention and management of shock states. Your efforts and dedication in presenting educational materials in this journal are commendable. Best wishes from, Farahnaz Fallahian.
Dear Maria Emerson, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews, Auctores Publishing LLC. I am delighted to have published our manuscript, "Acute Colonic Pseudo-Obstruction (ACPO): A rare but serious complication following caesarean section." I want to thank the editorial team, especially Maria Emerson, for their prompt review of the manuscript, quick responses to queries, and overall support. Yours sincerely Dr. Victor Olagundoye.

Dear Ashley Rosa, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews. Many thanks for publishing this manuscript after I lost confidence the editors were most helpful, more than other journals Best wishes from, Susan Anne Smith, PhD. Australian Breastfeeding Association.

Dear Agrippa Hilda, Editorial Coordinator, Journal of Neuroscience and Neurological Surgery. The entire process including article submission, review, revision, and publication was extremely easy. The journal editor was prompt and helpful, and the reviewers contributed to the quality of the paper. Thank you so much! Eric Nussbaum, MD
Dr Hala Al Shaikh This is to acknowledge that the peer review process for the article ’ A Novel Gnrh1 Gene Mutation in Four Omani Male Siblings, Presentation and Management ’ sent to the International Journal of Clinical Case Reports and Reviews was quick and smooth. The editorial office was prompt with easy communication.

Dear Erin Aust, Editorial Coordinator, Journal of General Medicine and Clinical Practice. We are pleased to share our experience with the “Journal of General Medicine and Clinical Practice”, following the successful publication of our article. The peer review process was thorough and constructive, helping to improve the clarity and quality of the manuscript. We are especially thankful to Ms. Erin Aust, the Editorial Coordinator, for her prompt communication and continuous support throughout the process. Her professionalism ensured a smooth and efficient publication experience. The journal upholds high editorial standards, and we highly recommend it to fellow researchers seeking a credible platform for their work. Best wishes By, Dr. Rakhi Mishra.

Dear Jessica Magne, Editorial Coordinator, Clinical Cardiology and Cardiovascular Interventions, Auctores Publishing LLC. The peer review process of the journal of Clinical Cardiology and Cardiovascular Interventions was excellent and fast, as was the support of the editorial office and the quality of the journal. Kind regards Walter F. Riesen Prof. Dr. Dr. h.c. Walter F. Riesen.

Dear Ashley Rosa, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews, Auctores Publishing LLC. Thank you for publishing our article, Exploring Clozapine's Efficacy in Managing Aggression: A Multiple Single-Case Study in Forensic Psychiatry in the international journal of clinical case reports and reviews. We found the peer review process very professional and efficient. The comments were constructive, and the whole process was efficient. On behalf of the co-authors, I would like to thank you for publishing this article. With regards, Dr. Jelle R. Lettinga.

Dear Clarissa Eric, Editorial Coordinator, Journal of Clinical Case Reports and Studies, I would like to express my deep admiration for the exceptional professionalism demonstrated by your journal. I am thoroughly impressed by the speed of the editorial process, the substantive and insightful reviews, and the meticulous preparation of the manuscript for publication. Additionally, I greatly appreciate the courteous and immediate responses from your editorial office to all my inquiries. Best Regards, Dariusz Ziora

Dear Chrystine Mejia, Editorial Coordinator, Journal of Neurodegeneration and Neurorehabilitation, Auctores Publishing LLC, We would like to thank the editorial team for the smooth and high-quality communication leading up to the publication of our article in the Journal of Neurodegeneration and Neurorehabilitation. The reviewers have extensive knowledge in the field, and their relevant questions helped to add value to our publication. Kind regards, Dr. Ravi Shrivastava.

Dear Clarissa Eric, Editorial Coordinator, Journal of Clinical Case Reports and Studies, Auctores Publishing LLC, USA Office: +1-(302)-520-2644. I would like to express my sincere appreciation for the efficient and professional handling of my case report by the ‘Journal of Clinical Case Reports and Studies’. The peer review process was not only fast but also highly constructive—the reviewers’ comments were clear, relevant, and greatly helped me improve the quality and clarity of my manuscript. I also received excellent support from the editorial office throughout the process. Communication was smooth and timely, and I felt well guided at every stage, from submission to publication. The overall quality and rigor of the journal are truly commendable. I am pleased to have published my work with Journal of Clinical Case Reports and Studies, and I look forward to future opportunities for collaboration. Sincerely, Aline Tollet, UCLouvain.

Dear Ms. Mayra Duenas, Editorial Coordinator, International Journal of Clinical Case Reports and Reviews. “The International Journal of Clinical Case Reports and Reviews represented the “ideal house” to share with the research community a first experience with the use of the Simeox device for speech rehabilitation. High scientific reputation and attractive website communication were first determinants for the selection of this Journal, and the following submission process exceeded expectations: fast but highly professional peer review, great support by the editorial office, elegant graphic layout. Exactly what a dynamic research team - also composed by allied professionals - needs!" From, Chiara Beccaluva, PT - Italy.

Dear Maria Emerson, Editorial Coordinator, we have deeply appreciated the professionalism demonstrated by the International Journal of Clinical Case Reports and Reviews. The reviewers have extensive knowledge of our field and have been very efficient and fast in supporting the process. I am really looking forward to further collaboration. Thanks. Best regards, Dr. Claudio Ligresti
Dear Chrystine Mejia, Editorial Coordinator, Journal of Neurodegeneration and Neurorehabilitation. “The peer review process was efficient and constructive, and the editorial office provided excellent communication and support throughout. The journal ensures scientific rigor and high editorial standards, while also offering a smooth and timely publication process. We sincerely appreciate the work of the editorial team in facilitating the dissemination of innovative approaches such as the Bonori Method.” Best regards, Dr. Matteo Bonori.

I recommend without hesitation submitting relevant papers on medical decision making to the International Journal of Clinical Case Reports and Reviews. I am very grateful to the editorial staff. Maria Emerson was a pleasure to communicate with. The time from submission to publication was an extremely short 3 weeks. The editorial staff submitted the paper to three reviewers. Two of the reviewers commented positively on the value of publishing the paper. The editorial staff quickly recognized the third reviewer’s comments as an unjust attempt to reject the paper. I revised the paper as recommended by the first two reviewers.

Dear Maria Emerson, Editorial Coordinator, Journal of Clinical Research and Reports. Thank you for publishing our case report: "Clinical Case of Effective Fetal Stem Cells Treatment in a Patient with Autism Spectrum Disorder" within the "Journal of Clinical Research and Reports" being submitted by the team of EmCell doctors from Kyiv, Ukraine. We much appreciate a professional and transparent peer-review process from Auctores. All research Doctors are so grateful to your Editorial Office and Auctores Publishing support! I amiably wish our article publication maintained a top quality of your International Scientific Journal. My best wishes for a prosperity of the Journal of Clinical Research and Reports. Hope our scientific relationship and cooperation will remain long lasting. Thank you very much indeed. Kind regards, Dr. Andriy Sinelnyk Cell Therapy Center EmCell
